The XOR encryption model
We will implement a very basic symmetric XOR encryption algorithm (gamming) and study the error rate.
Task description
Symmetric ciphers allow you to encrypt and decrypt messages using the same key. This is a very common component of encryption algorithms. Despite the fact that it is vulnerable to frequency analysis and many other matching methods.
Operation XOR (exclusive OR) performs the following operation on the input bits:
| a | b | XOR(a, b) |
|---|---|---|
| 1 | 1 | 0 |
| 0 | 1 | 1 |
| 1 | 0 | 1 |
| 0 | 0 | 0 |
The following scheme allows you to experiment with messages in a string representation, compare them and calculate decryption errors.
- The first XOR block performs encryption, then the ciphertext bits go along the signal line.
- The second XOR block performs decryption using the same key bytes as the first XOR block.
If transmission delays occur in the intermediate channel, a comparison of the Message and Ciphertext in the block Error Rate Calculation you can do this with an offset (see block settings).
Launching the model
The model can be started using software control commands.:
# We will load the model if it is not already open on the canvas.
if "xor_cipher_model" ∉ getfield.(engee.get_all_models(), :name)
engee.load( "$(@__DIR__)/xor_cipher_model.engee");
end
model_data = engee.run( "xor_cipher_model" );
Output the number of decryption errors:
print( "Number of decryption errors: ", Int32(model_data["Number of errors"].value[end]) )
Let's see which bits came after decryption.:
out_vector = collect(model_data["Decoding"]).value;
received_bytes = [ UInt8(evalpoly(2, reverse(out_vector[1+8*start:8*start+8]))) for start in 0:div(length(out_vector),8)-1 ]
To assemble a Unicode string from bytes:
String( received_bytes )
We received the same message at the exit that we sent at the entrance.
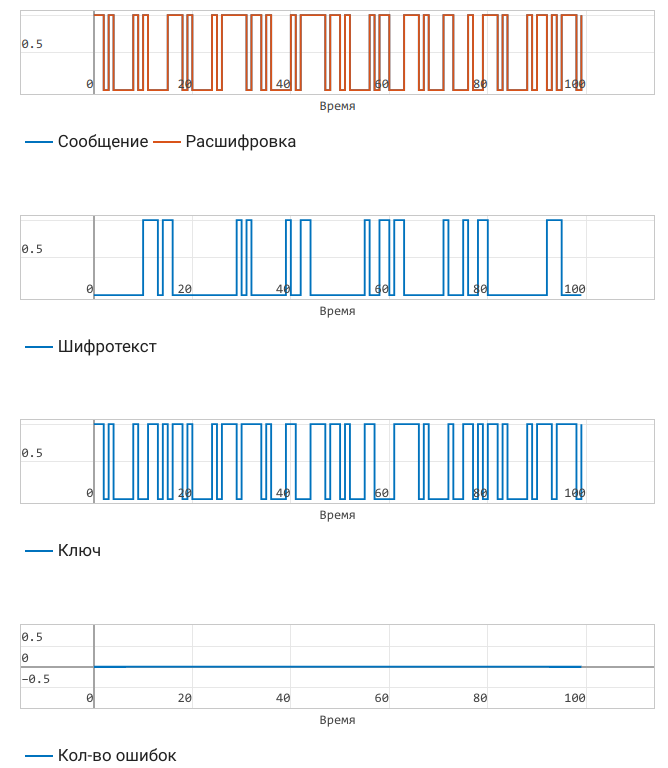
The result of the model can be studied without scripts, it is enough to study the information on the Graphics panel.
.png)
As we can see, the error rate is not increasing because the same key bits are used for encryption and decryption, and also because there is no noise in the channel.
Conclusion
We have created an environment to study the simplest cryptographic algorithm XOR, also called gamming. The model performs encryption and decryption, it is easy to add noise and bias to it, and as further steps you can try to perform a frequency analysis.